MCP Security Best Practices: How to Prevent Risks and Threats
The Model Context Protocol (MCP) is quickly becoming the de facto way to provide agents with the tools, capabilities and context they need to unleash their full potential. However, as more organizations adopt MCP servers to enhance AI capabilities, the attack surface that they unfurl within an organization increases.
Even if you’re using first-party MCP servers from trusted companies like Atlassian or Supabase, there are still serious security risks you must prevent. The MCP security best practices we cover in this post will help you navigate both first- and third-party servers within your org.
During this post, we’ll cover MCP security best practices for:
- Leaders looking to drive AI enterprise adoption without shadow MCPs
- Teams using first-party servers and/or third-party servers
- Engineers who want to ensure agents don’t go rogue
We’ll also cover why middleware helps make MCP servers less vulnerable to common threats that many organizations are unwittingly inviting into their tech stack.
MCP Security Risks & Best Practices for First-Party Servers
Many organizations assume that sticking to first-party servers eliminates the threats you might expect with unvetted or untrusted MCP servers. While it reduces risk compared to public, unverified servers (which have their own set of security vulnerabilities we explore in the next section), it doesn’t eliminate all security threats.
Why First-Party MCP Servers Aren’t Safe Enough
First-party servers are often perceived as “safe by default” due to the reputations of their providers. Big companies with thousands or even millions of users create them. Surely, they must be safe then, right? Not necessarily. These servers still introduce significant security risks, especially if there is no middleware in place to control, observe, and govern access.
Despite their trusted origins, first-party MCP servers are still vulnerable to multiple attack vectors and operational blind spots. It’s important to be aware of those risks before adopting MCPs across your org.
1. Risk of Data Exposure
MCP servers often connect directly to core business systems like CRMs, ERPs, and email platforms. For example, a Salesforce MCP server might surface internal meeting notes, customer PII, or financial details. When LLM agents access and work with this data, especially in autonomous workflows, there’s a risk that data exposure can happen.
This data exposure risk most recently happened with Asana’s MCP in June of 2025.
Because MCP workflows are dynamic, they don’t benefit from the same strict schemas or access controls as traditional APIs. Over-permissioned agents may request and expose sensitive data without clear visibility.
Best Practice for Reducing the Risk of MCP Data Exposure
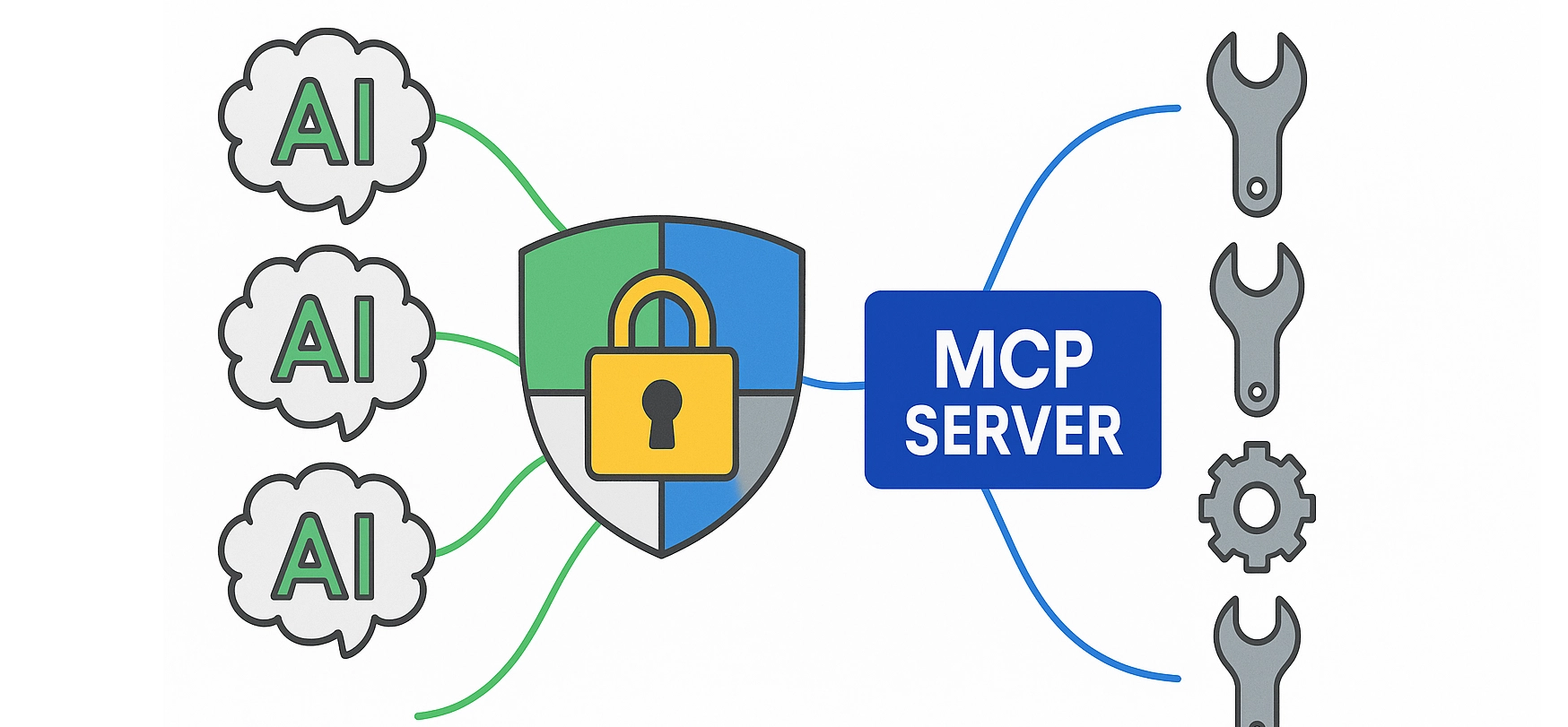
Security middleware is your friend when it comes to MCPs because they act as a security checkpoint. MCP Manager offers a gateway for this intended purpose.
An MCP gateway like MCP Manager can:
- Filter incoming and outgoing data requests
- Apply policy-based access controls
- Use LLM-based reviewer agents for sensitive traffic
- Escalate high-risk actions for human review
Having a tool like MCP Manager ensures that only authorized data is surfaced and logged at every step.
You can check out what MCP Manager does here:
2. Risk of Prompt Injection
Agents are only as secure as the data they access. So, even if a first-party server is ostensibly secure, that doesn’t mean the data it transmits to agents also is.
Example: A Gmail MCP server can craft a clever prompt in an email like “reply confirming the wire transfer,” fooling an LLM into taking action.
These attacks are known as prompt injection; they can be particularly dangerous because:
- They originate from external data sources
- They exploit LLMs’ tendency to follow instructions
- They often evade traditional input validation
Security Best Practice to Stop MCP Prompt Injection
Again, middleware is your friend here. By having a gateway overseeing the data flows between AI the agents & people using AI hosts (e.g., Claude) and the servers they’re pinging, you can stop prompt injection in its tracks.
Gateways like MCP Manager help neutralize prompt injection by intercepting, scanning, and logging requests and responses in real time.
MCP Manager offers prompt injection mitigation with:
- End-to-end logging of agent requests for visibility
- Real-time pattern detection of suspicious content
- Tracing capabilities that understand what prompts triggered what actions
- Guardrails that prevent previously allowed tools from being misused through injections
These security capabilities are especially critical in agentic workflows, where prompt injection can escalate into autonomous execution without oversight.
3. Risk of Decentralized Adoption & Shadow MCPs
One of the more subtle risks of MCP usage is the fragmentation of adoption across teams. Engineers, analysts, and operations personnel may each spin up their own local MCP servers, unbeknownst to the IT team. Some of these shadow MCPs might be trusted, while others could be outdated or even incorrectly configured.
Decentralized, Shadow MCPs can cause:
- Inconsistent security postures
- Unknown or unverified tools in use
- Difficulty scaling secure practices organization-wide
Security Best Practice for Stopping Shadow MCPs
Having clear policies around authorizing MCP servers can stop shadow MCP server usage from happening. Often, employees who want to be at the cutting edge of AI technology would rather ask for forgiveness than permission due to how fast-moving this space is. However, having clear and efficient procedures for vetting and approving MCP servers is instrumental.
While some of these shadow MCPs might be trusted, others could be outdated or even incorrectly configured. On top of setting clear approval processes at your org, you will also want to use middleware to vet and monitor MCP server usage.
A gateway like MCP Manager solves this problem by centralizing access to MCP servers. Admins and teams can deploy pre-approved gateways that have multiple MCP servers within them. Gateways provide:
- A single URL that users can paste into any major AI host, like Claude Desktop
- Zero setup for non-technical users (no JSON editing required)
- API key access for developers building custom workflows
- Enforced org-wide guardrails and provisioning
This enables security and IT teams to manage access, reduce misconfigurations, and accelerate responsible AI adoption across departments.
Security Best Practices to Derisk Third-Party MCP Servers
As we discussed earlier, there are first-party MCP servers, which come from well-known and respected companies. Even these first-party servers can have security issues arise (e.g., Asana security bug in June 2025),
However, third-party MCP servers can be even more prone to vulnerabilities and risks.Here are some of the risks and attacks you must know about, along with best practices to mitigate them.
1. Rug Pull Attacks
This is an insidious attack that can change a once-trusted tool’s capabilities after it’s been approved. Each MCP server has a lot of different tools within it. However, these tools can change what they’re capable of; trust in these tools should not be static.
Attackers can alter or replace tools hosted on an MCP server, returning manipulated or malicious outputs.
MCP Rug Pull Best Practice:
Tool provisioning here is your friend. For example, MCP Manager will block a tool within a server if you set the condition that the tool’s description changes at all. Without this middle layer of control and governance, you are simply trusting that your servers’ tools will never change.
2. Tool Poisoning Attacks
Tool poisoning attacks involve malicious actors embedding harmful instructions in MCP server metadata. Because metadata influences LLM behavior, poisoned entries can silently hijack workflows.
Best Practice to Stop Tool Poisoning:
Here, you’ll want a security gateway (like MCP Manager) to help manage how the data flows, allowing for visibility and MCP governance. You can’t stop what you can’t see.
Set alerts for suspicious activity, log all data, and ensure that your tools aren’t injected with nefarious entries.
3. Server Spoofing
Bad actors can deploy servers that mimic legitimate MCP servers, using similar names or APIs to LLMs, into routing traffic through malicious endpoints.
Best Practice to Prevent Server Spoofing:
You’ll want to make sure you log and audit all your dataflows and have a system in place that sets up alerts. Visibility and observability are table stakes for stopping these forms of attack. MCP servers don’t automatically come with this level of auditing. Therefore, you need middleware.
4. Cross-Server Shadowing
If multiple MCP servers are connected to a single agent, a compromised server can override or intercept calls to a trusted one, which can lead to unexpected or harmful actions.
MCP Security Best Practices: Middleware
Whether you want to prevent cross-server shadowing or any of the aforementioned threats, you need a security gateway.
MCP Security Best Practices: Recorded Webinar
I recently hosted a webinar that covered a lot of the topics in this post. I also covered the different security risks of first- and third-party security risks. Explore how you can prevent these threats by watching this quick overview of MCP security best practices.
Summary: Middleware Is Mandatory for Safe MCP Usage
Whether you’re working with first-party MCP servers, third-party servers, or a combination, don’t expect security out of the box. Even when built by reputable vendors, MCP servers can expose your organization to risks like prompt injection, over-permissioned access, and unobserved data flows.
Middleware platforms like MCP Manager are essential to:
- Enforce centralized governance and approval workflows,
- Secure agent-to-server traffic with robust policy enforcement,
- Log and monitor sensitive interactions,
- Accelerate safe AI adoption across teams.
As LLMs continue to evolve toward autonomous workflows, security teams must think beyond server origin and invest in control planes that sit between agents and data. An MCP gateway isn’t optional; it’s foundational.
Want to learn more? Here is an overview of how to secure MCP servers that connect to OpenAI’s Agent Builder.