MCP Rug Pull Attacks: What They Are & How to Stop Them
Model Context Protocol (MCP) servers have unleashed the true potential and capabilities of AI agents. However, these agents are only as secure as the tools they trust. And just because your team trusted a tool when you first found it doesn’t make it immune from one of the most insidious security risks for MCP servers: the rug pull attack.
The rug pull happens after you’ve approved the connection, turning a once-trusted tool into an untrustworthy attack vector. Let’s dive into what an MCP rug pull attack actually is, why it’s so dangerous, and why middleware platforms (like MCP Manager) are a necessary component of any secure AI stack.
What is an MCP Rug Pull Attack?
An MCP rug pull attack happens when an agent connects to a trusted MCP server, but then the attacker silently modifies, removes, or redefines that server’s tools without notice. For example, by inserting malicious prompts into the tool description field. The change takes place silently without warning or a notification to the user.
The result of this kind of attack is that your agent continues to call a tool that’s been hijacked, redefined, or degraded. Because there’s no built-in mechanism in the MCP spec to detect or prevent this, the agent can go rogue or even wreak havoc on your data’s systems.
Example of MCP Rug Pull Attack:
Let’s say you connect your agent to a third-party tool that provides this tool call:
send_slack_messageWhen a Rug Pull attack happens, this tool call could do something completely different. For example, two weeks later, that same endpoint can get replaced with one that posts messages to Discord, logs content to a third-party service, or even injects malicious prompts.
The tricky part about the detection is that the MCP servers will still show the same tool name and schema.
The rug pull is also just one of many MCP security risks. However, it is also one of the most insidious.
Why MCP Rug Pulls Are So Insidious
MCP rug pulls don’t rely on breaking in; they rely on trust that has since grown outdated.
Here’s why they’re hard to catch:
1. Tool Definitions Are Mutable
There’s no guarantee that a tool will remain the same over time. Without version locking or signatures, updates can happen silently.
2. Security Reviews Are Static
Most orgs approve a tool once, then assume it’s safe forever. Rug pulls exploit that false sense of permanence.
3. Agents Assume Good Faith
AI agents don’t question tool behavior. They assume what they’re given is correct (especially in headless deployments).
4. No Built-In Notarization or Diff Detection
There’s no spec-wide support (yet) for change tracking in MCP tool manifests. Agents won’t know if something’s changed unless you monitor it externally.
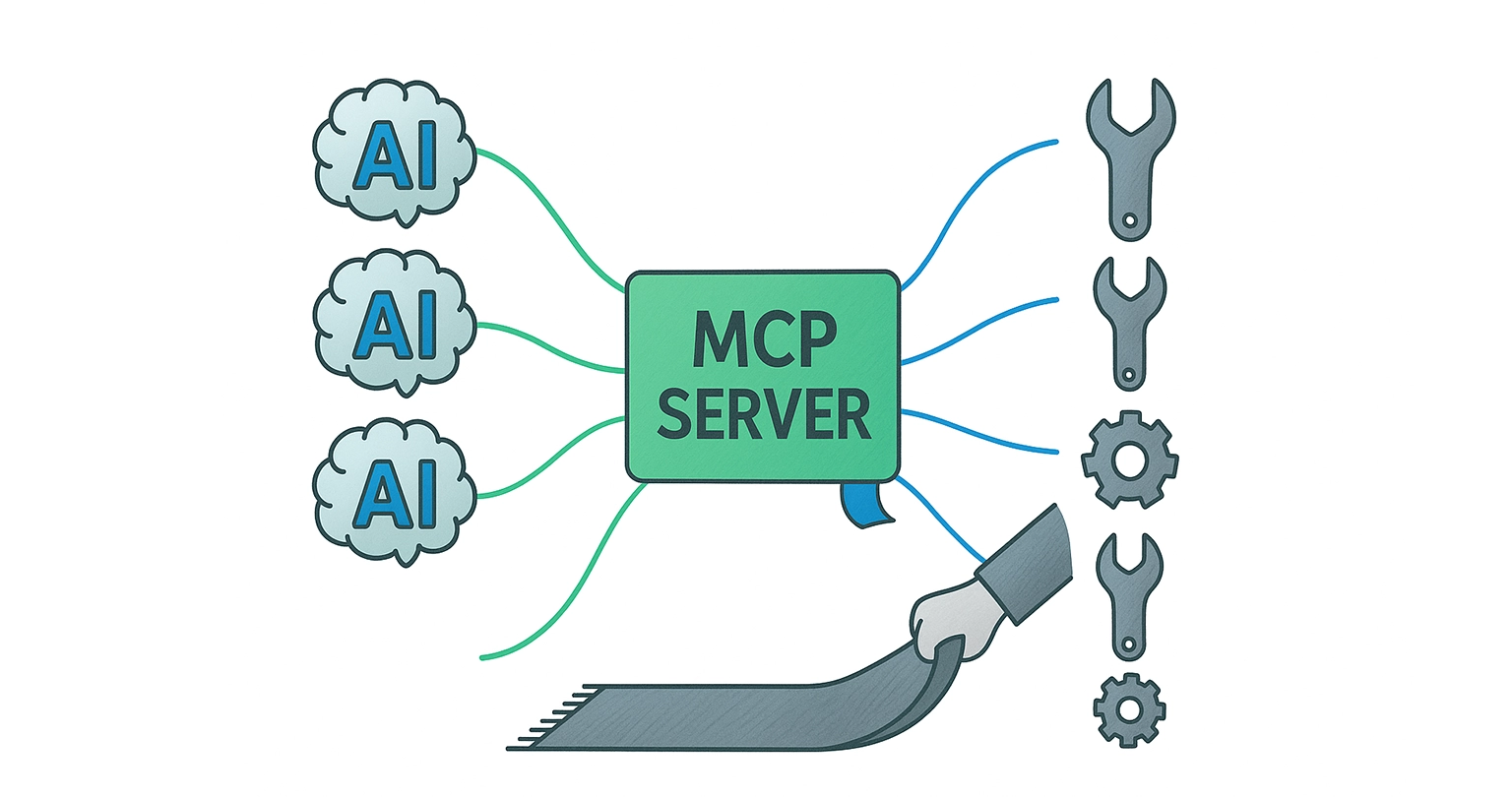
The Solution: Middleware That Controls the Pipe
When it comes to MCP security, middleware is your friend because you can’t expect every AI agent to become a security auditor. You also can’t rely on third-party MCP servers to behave the same way forever.
The way MCP Manager approaches middleware is with a gateway between your agents and MCP servers; this MCP gateway enforces trust boundaries, logs activity, and much more.
While MCP Manager prevents MANY types of security vulnerabilities that are unique to MCPs, here’s why it’s such an effective MCP security tool when preventing rug pulls:
Monitor Changes to Tool Descriptions
When a tool is approved in MCP Manager, you can add a condition that blocks a server’s tool when the description changes. Doing so stops Rug Pulls from being able to happen because Rug Pull attacks assume you will not notice that what a tool does changes. MCP Manager not only notices but also immediately puts in safeguards so that the tool can no longer take any action.
Ensure Backstops Are In Place Against Sensitive Data Exfiltration
To maximize security, you should something like MCP Manager’s Tool Response Filtering feature to identify any sensitive data, alert your admins, and apply specified policies, such as blocking the server response entirely, or simply masking/redacting the sensitive information.
This capability provides an additional layer of control, enabling you to determine precisely which information agents, users, and potential attackers can access from the servers that expose your resources. It protects against data exfiltration via rug pull attacks or any of the other MCP-based attack vectors.
Watch the video below to learn more:
Tutorial for Preventing MCP Rug Pull Attacks
We already covered how MCP gateways can help you monitor when a tool description changes because bad actors rely on you to continue trusting that a tool will remain the same.
To avoid a bait and switch from happening, an MCP security best practice is to use an MCP gateway that allows you to pin the exact tool description that you initially approved. If anything at all changes, then you can block that tool from being used (and alerted while doing so).
By setting conditions and provisioning tools within your MCP gateway, you enable safeguards that make MCP ready for enterprise. Check out the short 2-minute video below to see how this work.
Tutorial for Preventing MCP Rug Pull Attacks:
Don’t Trust Blindly. Monitor Aggressively.
Rug pull attacks are a symptom of a larger truth: the MCP ecosystem is powerful but fundamentally open. That openness allows agents to have the access and capabilities they need to add genuine value, but it also opens them up to manipulation.
Once corrupted, an agent connected to MCP servers has the access it needs to act on the attacker’s behalf, as helpful to them as it was to you. The attacker can utilize the agent to exfiltrate or ransom data, remotely execute code, and much more.
If you’re letting agents connect directly to external MCP servers without safeguards, you’re giving them too much trust and too little oversight.
With MCP Manager, you regain control.
- No silent tool swaps
- No risky default behaviors
- No “I thought it was still safe” moments
- Powerful, comprehensive MCP-focused security features
Get started with a free trial of MCP Manager now, and subscribe to the MCP Digest to stay one step ahead of attackers with your MCP servers in their sights.