We make MCP ready for production and ready for enterprise.
Let’s go over the deployment, observability, and security solutions that MCP Manager
offers to make AI work effectively for your business.
MCP Manager Makes AI Powerful & Secure
Our team and platform help businesses deploy, secure, and scale MCP.
MCP and AI
Deployment Services
Save time and headaches by working directly with our engineers, who are experts at getting secure and scalable MCP servers into production. Deploy with clicks, not code, and save your team countless hours of work.
Observability, Dashboards, and Audit Logs
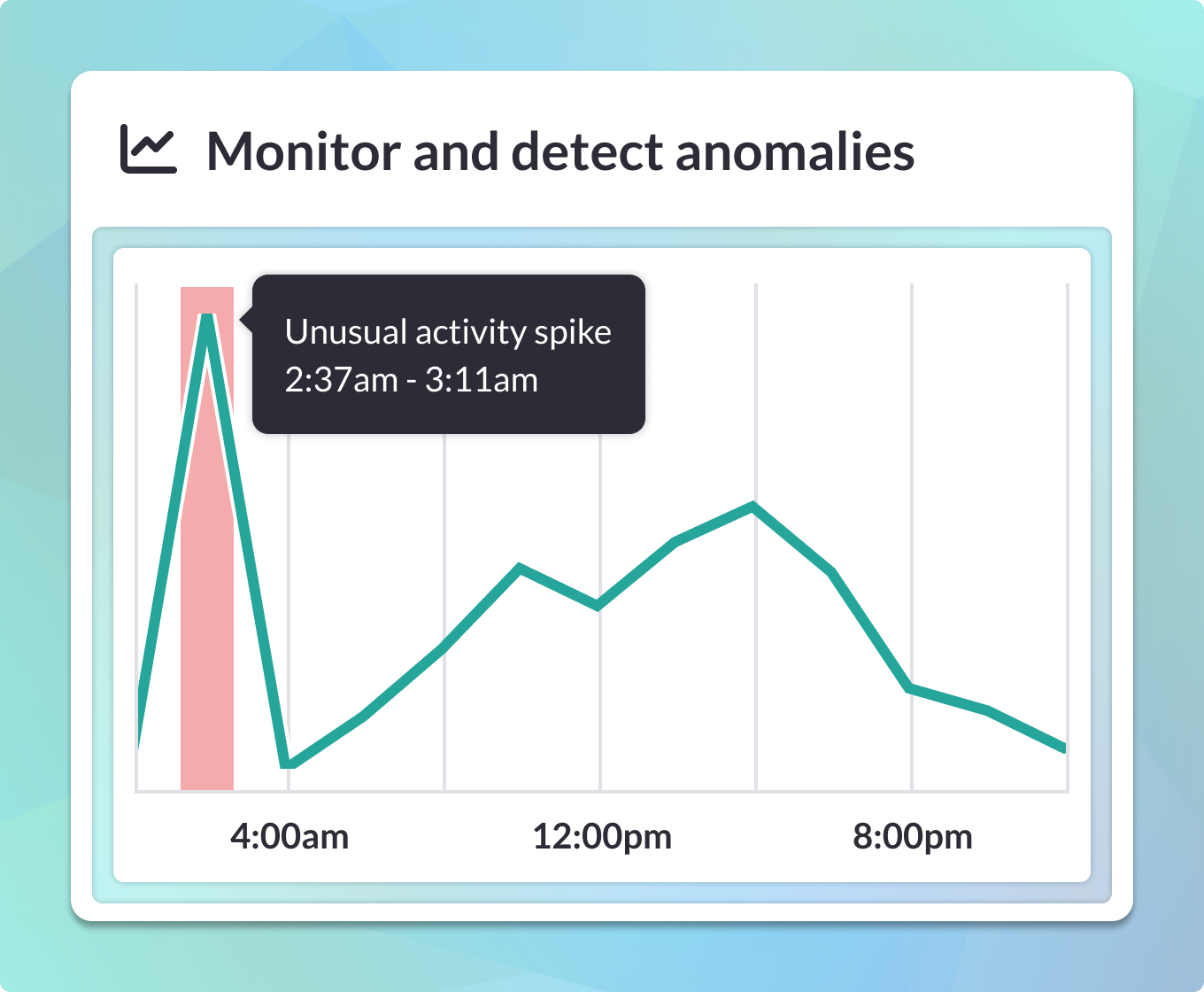
You can’t fix or optimize what you can’t see. MCP doesn’t provide insightful logs out of the gate. Gain visibility for debugging, securing, and monitoring MCP activity within your organization.
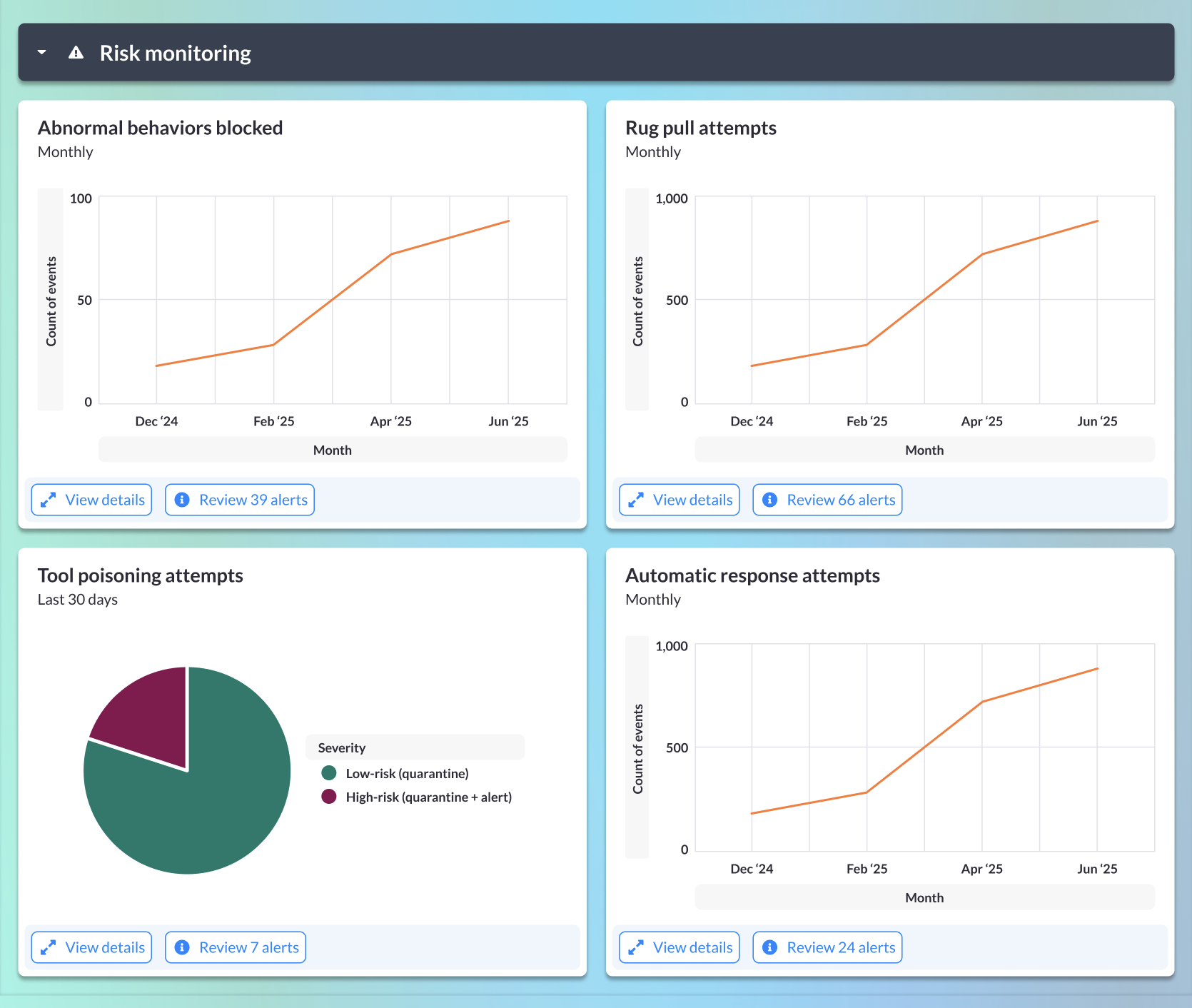
Security Features to Prevent MCP Risks
MCP servers are vulnerable to unique security threats, including prompt injection and rug pull attacks. Our platform offers protection against these threats and real-time security monitoring.
We Detangle the Complexity of MCP Deployment
There isn’t just one type of MCP deployment, and most teams use a combination of MCP deployments.
Our team works directly with businesses to make MCP work exactly as they need.
MCP Manager Provides Observability and Security
Gateways to Protect Data from External Threats
MCP Manager gateways regulate the flow of data between AI hosts and MCP servers. Without them, your business is exposed to devastating security risks. Each gateway governs access, behavior, monitoring, and visibility.
Robust Policies for Hosts, Servers, and Data
Without robust policies, your network is vulnerable to catastrophic breaches. MCP Manager enforces global policies around things like:
- Activity logging
- Approvals
- Alerts & responses to detected threats
Control Access to MCP Features That Expose Vulnerabilities
MCP Manager lets you set strict policies for approving or restricting MCP features. Without these controls, your system is exposed to serious risks. Enforce guardrails on:
- ✏️ Prompts agents are allowed to send
- 📁 Resources they can access or request
- 🛠️ Tools they’re permitted to use
Audit Logs: Essential for Visibility and Security
Gain end-to-end, verbose logs of all MCP traffic to ensure that you have an audit of all communications between the host, AI agents, gateway, and MCP servers and to power your reports and alerts.
You can turn logging off or on. Admins can access these logs by downloading a CSV file that details all tool calls.