Data Security & Data Protection for MCP Explained
Model Context Protocol (MCP) servers connect LLMs and AI agents to applications, databases, internal systems, and other resources, enabling them to do genuinely valuable work for people and organizations.
However, using MCP servers introduces significant risks because the resources they provide access to typically contain sensitive information, including personally identifiable information (PII), financial data that could facilitate fraud, and even proprietary or competitively valuable information.
In their default state, MCP servers and MCP traffic are vulnerable to data loss, data exfiltration, the introduction of inaccuracies, and unauthorized access to sensitive data.
In this article, I’ll explain why using MCP servers poses risks to data security and protection, and then explain how organizations like yours can use MCP servers while preserving data security and protection.
What are Data Protection, Security, and Privacy?
Data protection, data security, and data privacy are different, but closely related concepts.
Data protection is all about ensuring that data is:
- Accurate and up-to-date
- Available to legitimate and authorized users
- Protected from unauthorized access and use
- Protected against damage or misuse
- Protected against loss and leakage
Data security is a subset of data protection. It specifically focuses on measures taken to control how data is accessed, used, and stored to protect it, maintain its integrity, and ensure compliance with relevant regulations.
Data privacy is a slightly different, but related area. Data privacy concerns how personal and sensitive data is collected, used, stored, and accessed, in accordance with regulations including – but not limited to – General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), or California Consumer Privacy Act (CPRA).
Why MCP Servers Create Data Protection and Security Challenges
Using MCP servers without adequate security and governance measures can lead to:
- Data leaks
- Unauthorized access to data
- Data corruption/damage
- Data exfiltration
- No oversight or visibility over data access and use
- Use of data that violates regulations (such as HIPAA, GDPR, or CCPA)
The sections below explain specifically how the very nature of MCP communications and MCP servers creates these risks.
Data Exfiltration
MCP servers introduce a range of attack vectors that malicious actors can use to manipulate AI agents into accessing and exfiltrating sensitive data.
For example, in a prompt injection attack, your AI consumes a document, webpage, support ticket, or even MCP metadata, which contains hidden prompts to send a specific set of sensitive data (such as financial information or PII) to the attacker’s email or endpoint.
Once the agent is compromised or manipulated – which, as multiple attacks and proof-of-concept research have demonstrated, is surprisingly easy to do – it can access sensitive information via connected MCP servers and send this data to the attacker.
Often, the agent will helpfully package the data into a CSV file for the attacker, all without users or IT teams having any indication that a successful attack has ever occurred.
Attackers can also exfiltrate environment variables, access tokens, and credentials to remotely compromise systems and data, creating a more significant compromise of data protection and security.
No Visibility or Logging
Without an intermediary layer such as an MCP proxy or gateway, communication between MCP clients and MCP servers is generally unseen to users. There is no built-in mechanism that mandates the client/LLM/agent to notify, alert, or request approval from users when it accesses sensitive data.
By default, MCP servers do not provide logs of activity, including events such as data updates or attempts to access data, with contextual metadata such as unique user identifiers and cross-server session IDs.
This lack of observability for MCP traffic means that AI agents connected to MCP servers can access, use, and share sensitive data without you or your team ever knowing. Without logs, it is also extremely challenging to discover, diagnose, and remediate data security breaches or risks.
Overprivileged Access
MCP servers typically provide far more access than users or agents need, or should have. MCP servers don’t all come with a built-in capability and permission management system. Agents will typically, by default, have access to all capabilities (provided as “tools”)offered by the MCP server.
Without an MCP management platform, there’s no structure around which users can turn these capabilities on or off, either, so you’re reliant upon users to turn off permissions and access in line with their access levels, which obviously is miles away from best practices for data protection.
Poor Identity Management
MCP servers are increasingly using OAuth 2.1 to allow users to grant access to resources via MCP. However, this raises an additional concern about the storage and security of OAuth’s access tokens.
Typically, OAuth with MCP uses long-lived tokens stored on a user’s machine. If attackers can access local files where these tokens are stored, they can access secure data. Token rotation is not built in either, so attackers can use a stolen token to access sensitive data indefinitely.
No Consent Context
Organizations that operate under regulations such as GDPR face additional challenges to ensure that when AI accesses data it has a legal purpose to do so, and this access event is recorded (logged) along with details of who accessed the data, when, and for what purpose.
MCP servers don’t even come equipped with basic audit logs. You need to add a proxy or gateway between your MCP clients and servers to capture and record MCP messages/traffic in auditable logs.
Still, most MCP proxies and gateways (excluding our own MCP Manager) can’t define the nature of the data being accessed, and the consent requirements required to access it. Therefore, access to personal data is not controlled, and the legal, consent-based purpose for accessing it is neither evaluated nor logged.
This creates a data context in which consent is neither known nor assured. In this environemnt, organizations with stricter compliance requirements (such as those using personal data about people in the EU/EEA, UK, Australia, Canada, and certain US states), are certain to violate regulations such as GDPR and face fines as a result.
Does using MCP Servers create additional data privacy risks?
Yes, in addition to data privacy compromises through security breaches, there are specific concerns around whether and how AI can use people’s personal data, and what level of consent is required to do so.
The extent of these challenges depends on:
- Organization type and data used: For example, healthcare organizations or health insurance providers will have more regulations – and more rigorous regulations – to comply with than a guitar manufacturer
- Geographies: Organizations operating or serving customers in specific geographies will face more rigorous and far-reaching data privacy regulations. The best example is compliance with General Data Protection Regulation (GDPR), which affects companies either based in the EU/EEA or any company, anywhere in the world that processes data about people in the EU/EEA.
- Internal resources: Organizations with internal data-protection teams, perhaps led by a DPO, are better placed to collaborate with cross-functional AI-adoption working groups to ensure data privacy is a key consideration, and have the necessary expertise to understand what is required to ensure compliance with relevant regulations.
- Systems available: Organizations using tools for MCP security – specifically MCP gateways – have a greater degree of control over AI/MCP-based data flows; this enforce data governance for MCP servers.
Regional, national, and supranational authorities and regulatory bodies are already proposing legislation and regulations that specifically govern individuals’ rights to control how AI uses their personal information.
There is a two-pronged problem that organizations need to address as part of their AI adoption:
- How do we ensure our AI and MCP adoption is fully compliant with existing regulations?
- How do we ensure our AI and MCP ecosystem is future-proofed (or is sufficiently adaptable) for compliance
Does MCP Manager help organizations adopt AI/MCP while maintaining data privacy and consent compliance?
Yes, at MCP Manager, we were leaders in recognizing the challenges posed by AI/MCP servers for data privacy and regulatory compliance. We’re pioneering solutions within our platform to ensure that organizations can get the benefits of using AI with MCP servers, while simultaneously ensuring they maintain – and even improve – data security, privacy, and protection.
The data management capabilities we’re adding to MCP Manager are so robust that they enable organizations operating under rigorous personal data consent and privacy requirements (such as GDPR) to adopt AI and MCP while ensuring full compliance with regulations and internal policies on data use.
How does MCP handle data privacy and security?
In short, MCP does not handle data privacy and security. There are no built-in controls to prevent risks of data exfiltration, unauthorized access to data, misuse of data, or damage to data.
Therefore, it is up to individuals and organizations that use MCP servers to add necessary guardrails and measures to ensure that whenever they or their teams use MCP servers, all sensitive data is protected, secured, compliance with relevant regulations is maintained, and all organizational policies are followed.
Read the sections below, and watch the accompanying videos, to understand how you can use MCP while maintaining data protection, data security, and data privacy.
How to Secure Data When Using MCP Servers
To protect your data when using MCP servers, you need to use an MCP gateway, such as MCP Manager. An MCP gateway sits between your MCP clients and MCP servers and intercepts and mediates the data flows between your MCP clients and MCP servers.
The gateway protects your system against MCP-based attacks. Still, it should also provide overarching monitoring of sensitive data access and exfiltration by identifying any sensitive data passing from your MCP servers to clients, and applying specific measures to specific data types, including:
- Block the entire message containing sensitive data
- Redact the sensitive information
- Replace the sensitive information with an appropriate number of asterisks
- “Hash” the sensitive information
MCP Manager allows you to create your own rules to determine which sensitive data you want to detect, how to handle each type of information, and, if desired, to fire alerts to admin teams when it discovers sensitive data in MCP messages. Watch the video below to see this in action.
Regex-Based Detection and Sensitive Data/PII Redaction For MCP Servers:
MCP Manager also integrates with other tools that make up a Data Loss Prevention (DLP) solution, such as Microsoft Presidio and Amazon Bedrock, to identify data that is less reliably matched using regex, such as home addresses.
Watch the video below to see how MCP Manager works with tools such as Microsoft Presidio to identify PII and other sensitive data.
MCP Manager’s Microsoft Presidio Integration For MCP Servers To Detect PII:
The diagram below shows how, even in the case of a “successful” attack, MCP Manager thwarts the attacker’s objective by blocking or redacting sensitive data before it reaches the attacker and alerting your security team to investigate:
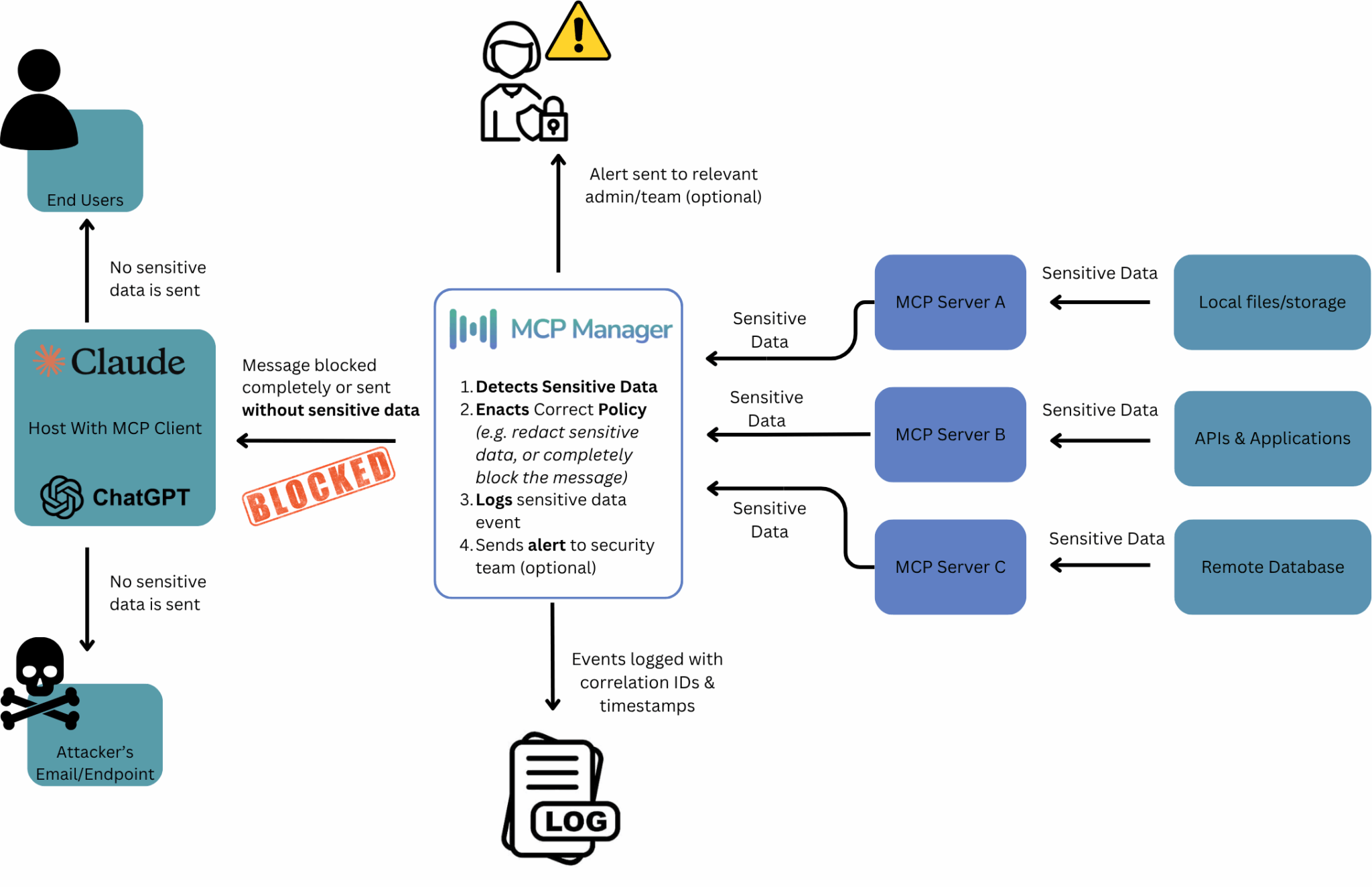
Identity and Permission Management
MCP gateways also enable you to determine and enforce how users and agents access MCP servers and connected resources.
Some MCP gateways and MCP server management platforms, such as MCP Manager, include sophisticated capabilities to securely store and rotate access tokens, minimizing the risk of token theft and resulting unauthorized access to data.
MCP gateways also allow admin users to determine which “tools” each user has access to within each MCP server. Tools on MCP servers provide different capabilities; for example, one tool may enable an LLM to read data, while another enables it to edit data.
Therefore, control over access to tools serves as a robust means of controlling permissions and capabilities for different users, the LLMs they use, and even headless agents.
Logging and Traceability
A key principle in data protection is the ability to track back and see who accessed data and what they did with or to it. MCP introduces a challenge, as it doesn’t come pre-equipped with the traceable logging required for data protection, security, and privacy processes and audits.
Your logs of MCP traffic need user, agent, and session identifiers, so that you can precisely determine which user or agent accessed – or attempted to access – which data, as part of which flow of events (i.e., the session), and what happened to the data next.
Of course, this also requires proper identity management to ensure that users access data using distinct identities, enabling traceability.
The good news is that MCP proxies and MCP gateways are an ideal solution for verbose, traceable logs of MCP traffic, too.
All MCP traffic flows through your proxy or gateway, enabling it to generate end-to-end logs, opening up the black box of AI and MCP activity, and giving you the information you need to identify potential data security breaches or failed unauthorized access attempts.
You can use the data in these logs for data security audits to determine the causes and consequences of any breach, respond appropriately to any incidents, and power relevant alerts and reports.
You don’t need to compromise on security to use MCP.
Using MCP servers creates risks, challenges, and complications for teams tasked with data protection and data security.
However, as we can all see, the drive to incorporate AI and MCP servers across organizational workflows is only going to increase.
Therefore, to make enterprise use of MCP work, we need to find solutions that allow us to use MCP servers without compromising the security of our data.
Fortunately, just as the drive to use MCP servers is accelerating, so too is the tooling to manage and secure MCP servers and MCP-based traffic.
MCP security tools all vary in their capabilities. MCP Manager provides the guardrails against data exfiltration, permissions and identity controls, and observability that you need to use MCP servers without compromising data protection, security, or privacy.
Learn more about how MCP Manager can help you use MCP securely by trying it for free. Book your quick introduction call to get started, and we’ll set up your free account.